At a time when cyber threats are increasingly sophisticated, understanding and i...
Are IPv6 Security enhancements safer than IPv4?

Myth: “IPv6 Security enhancements (such as IPsec) makes it safer than IPv4”
Truth: IPsec is an end-to-end security mechanism, providing authentication and encryption on the network layer.
Although developed in conjunction with IPv6, deployment problems with IPsec resulted in it not being widely adopted in the new IP stack. Similarly, IPv4 has had an adopted version of IPsec that can be implemented for extra security. It is unlikely that the adoption of IPv6 across the globe will stimulate a widespread use of IPsec.
Saying IPv6 is safer than IPv4 is in itself a challenging claim.
With the failure to make IPsec required with the implementation of IPv6, v6 and v4 have nearly identical encryption and authentication controls.
Recently, a remote code execution flaw in the Windows TCP/IP service was announced known as CVE-2022-34718 – see link. The vulnerability could allow an unauthenticated and remote attacker to execute code with elevated privileges on affected systems without user interaction.
However, only systems with IPv6 enabled and IPSec configured are vulnerable. Systems are not affected if IPv6 is disabled on the target machine.
“If a system doesn’t need the IPsec service, disable it as soon as possible” said Mike Walters, cybersecurity executive and co-founder of Action1. “This vulnerability can be exploited in supply chain attacks where contractor and customer networks are connected by an IPsec tunnel. If you have IPsec tunnels in your Windows infrastructure, this update is a must-have.”
How could an attacker exploit this vulnerability?
An unauthenticated attacker could send a specially crafted IPv6 packet to a Windows node where IPSec is enabled, which could enable a remote code execution exploitation on that machine.
Security device bypass via unfiltered IPv6 and tunneled traffic. Only a lack of knowledge is considered a bigger risk than the security products themselves. Conceptually its simple, security products need to do two things – recognize suspicious IPv6 packets and apply controls when they do. However, in practice this is hardly possible in v4 let alone an environment that may have rogue or unknown tunnel traffic. “There are 16 different tunnels and transition methods – not to mention upper layer tunnels like: SSH, IPv4-IPSec, SSL/TLS and even DNS,” says Joe Klein, Cyber Security Subject Matter Expert for the IPv6 Forum and Expert Cyber Architect at SRA International. “The first step is knowing what you’re looking for.” The current crop of security products used today, especially those converted from v4 to v6, haven’t necessarily matured enough to match the threat they’re protecting against.
GYTPOL’s got you covered!
You can easily remediate and disable IPv6 protocol using GYTPOL with Zero-Impact.
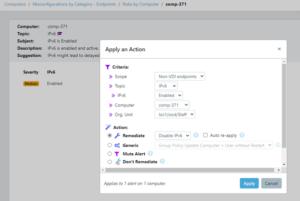
If you still want to do it manually, please take a look at this video:
About Author
Simone Lavi
Subscribe to
our Newsletter
We are ready to help you until and unless you find the right ladder to success.
Related Posts
Join over 25,000 in beating the failure of strategies by following our blog.
In the fast-paced world of technology, where innovation is a constant, it’s cruc...
4 minute read
Introduction:


Comments