Endpoint configurations are essential to good security. That’s always been the case, but it rings even truer with each p...
Secure endpoint configuration made simple
Reveal. Remediate. Relax.
All at the push of a button.
Reveal. Remediate. Relax.
All at the push of a button.
A function of context - misconfigurations are not design flaws, but deployment flaws. They are hard to define, mired in human error, and unpatchable.
with the potential to expose sensitive data, systems, and services
representing a huge, neglected stretch of the attack surface
accounting for more than eighty percent of all such attacks
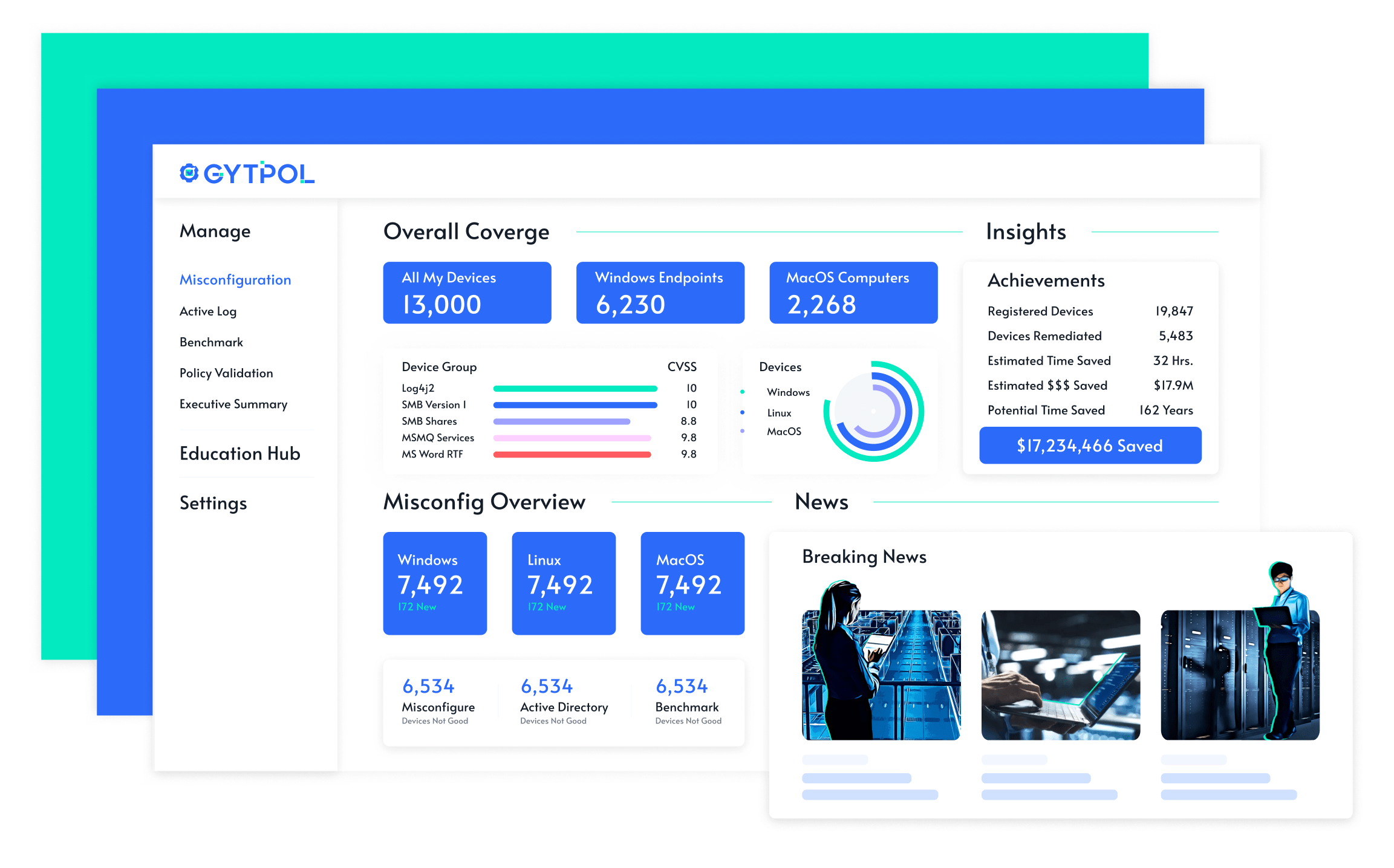
Deploying in minutes, GYTPOL automatically detects misconfigurations and makes it possible to bulk-remediate with a single click and without any risk of disruption to the business.
Reviewing your assets, active directory, MDM settings, and GPOs, misconfigurations are presented as alerts – sortable according to severity, device type, security group, or potential attack vector.
Defining a policy does not guarantee it will be effective or enforced. GYTPOL does. Take two steps forward no steps back – putting conflicting rules, incorrect GPO applications, and inert scripts in the rearview mirror.
GYTPOL assures compliance with any security standard for any device or fleet. Operating from within the designated framework (NIST, CIS, MITRE, etc.), action items are easily identified and advanced with click-to-enact/retract functionality.

Regardless of the operating systems and device types, GYTPOL has you covered. Whether it's Windows, macOS, or Linux, client, server, virtual machine, or cloud instances, you can rest easy knowing that your endpoint configurations are always secure.
Stay ahead of emerging threats – finding and fixing weaknesses in minutes rather than weeks. Assume a more proactive posture, moving from fire-fighting to fire-proofing. Get to the bottom of your to-do list, and reinvest your time savings in strategic projects.
Operate without fear of breaking things. GYTPOL eliminates the unknown, ruling-out or revealing any dependencies. Move forward with confidence knowing that you can rollback changes with one click.
GYTPOL gives us compliance, visibility, and remediation for 100% of endpoints and servers. All the time.
Global CISO, Check Point
GYTPOL has helped me deploy a Technical Security Baseline to all my endpoint devices globally.
Global VP and CISO, Eaton
GYTPOL gives our team incredibly detailed visibility into our global computing environment.
CISO, Colgate-Palmolive
GYTPOL helps me close security gaps – including those I didn’t know I had.
SVP & CISO, New American Funding
GYTPOL gives us the ability to fix problems in our environments without impacting our operations; it’s a real game-changer.
Associate CISO, The University of Kansas Health System
Look no further! Check out the GYTPOL Gazette for all the latest new, analysis, and configuration hardening advice
Endpoint configurations are essential to good security. That’s always been the case, but it rings even truer with each p...
Device configurations are one of the most important elements of your organizational security today. Why? For starters, s...
The world of cybersecurity is complex and ever-changing. But that doesn't mean there aren't any recurring themes or repe...
Don't let your endpoints become entry points. Start your free trial today!