Security leaders invest heavily in the front door: phishing defenses, malware de...
10 Cybersecurity Myths That Could Cost You Everything
Myths and misconceptions can be dangerous, especially in the world of cybersecurity. From treating group policies like gym memberships to the conviction that it just won't happen to you, there's a straight line from mistaken belief to mismanaged exposure. In this article, we’ll debunk 10 of the most damning cybersecurity myths — replacing them with grounded insights and best practices.
The fact that so many organizations remain so vulnerable to costly cybercrime, even after investing so much time and effort in their digital defenses, reflects the prevalence of misconceptions. And it's a harsh indictment.
Critical and Complicated: A Recipe for Cybersecurity Myths
It doesn't take a genius to see that decision-makers are building their businesses on faulty foundations when it comes to security and resilience. If they want to improve, they'll need to get to the bottom those misconceptions — understanding where they came from and where they went wrong.
Luckily, that's exactly what we'll be exploring in this article. Welcome to the myth-busting session your IT and security teams didn’t know they needed.
Myth #1: It Won't Happen to Us.
Too often, organizations don’t take proper precautions because they falsely think that they won’t be targeted or fall victim to attacks. In fact, many business leaders know they're leaving their organizations vulnerable but – looking at peer organizations – feel safe in the knowledge that they're no more exposed than others.
 That type of thinking is not only a fallacy, but it's incredibly dangerous; especially as a culture (and tolerance) of complacency becomes contagious once its normalized.
That type of thinking is not only a fallacy, but it's incredibly dangerous; especially as a culture (and tolerance) of complacency becomes contagious once its normalized.
It doesn't work for the ostrich and it won't work for you. It's also not supported by the facts: cyber-attacks hit 80% of businesses.
Cyberattacks happen to organizations of all sizes, in all verticals and geographies. Assuming your own safety just because is guaranteed to backfire over time.
The global financial toll? A projected $9.5 trillion.
Best practice: Regardless of what type of business or organization you have, you must protect yourself from cyberattacks and reduce your exposure. Always assume you are a target — because you are one.
Myth #2: If It Worked Then, It’ll Work Now.
It's very common for decision-makers to reason that since they've never been breached in the past, they won't be breached in the future either. It's a relatable logic as we all — at one time or another — adopt that sort of thinking. But that doesn't make it any more right.
It'd be like investing in Yahoo! today because it worked out well so well in 1999. It just doesn't naturally follow.
The threat landscape is constantly changing and there is a very real game of cat-and-mouse at play. If you’re not moving forward, you’re moving backward.
Your organization must always be prepared, able to tackle both known and emerging threats.
Best Practice: Effective security is a cycle of anticipation, adaptation, and action. Remedio helps organizations proactively detect and intelligently manage threats from yesterday, today, and tomorrow.

Myth #3: We're Safe Because We Do Annual Audits
This is the cyber equivalent of flossing once a year and calling it dental hygiene. We really hope you wouldn't do that.
Wish that there were, but the fact is there's no such thing as a one-and-done in cybersecurity. While regular audits are critical, they are insufficient without continuous monitoring and ongoing vigilance. A snapshot cannot protect you when both threats and your environment continue to evolve at a rapid pace. By the time the next audit rolls around, any one of a thousand potential points of exposure could have already been weaponized against you.
Best practice: Pair audits with continuous monitoring. Use Remedio to close the gap between check-ins and real-time visibility — detecting risky configuration drift the moment it happens.
Myth #4: We Just Patched for That Last Breach. We're Good Now.
Too many organizations content themselves with addressing the most recent or high-profile vectors — believing this will protect them. It will protect them against that one thing but, unfortunately, there are a million other threats it will do nothing to diminish.
You'd be justified to give yourself a pat on the back for fixing last month’s most exploited ransomware strain, but don't delude yourself into thinking that will help with your absentee access controls. This heavily reactive approach often overlooks deeper, more systemic exposure in the form of misconfigurations or outdated security policies — leaving the shortest attack paths wide open.
Case in point: A massive breach at Twitter occurred in 2020 when attackers used social engineering to trick employees into providing access to internal systems. They exploited overly broad internal permissions and hijacked numerous high-profile accounts, including those of Elon Musk, Barack Obama, Kim Kardashian, Bill Gates, and MrBeast.
The incident serves as a powerful that the attack surface stretches beyond our favorite focus areas and how no amount of patching can protect you from human error.

Best practice: Strong cybersecurity demands a holistic, proactive, continuous approach. Remedio helps you look beyond the flashy headlines and reinforce the fundamentals — like airtight configurations and smart access policies.
Myth #5: Once Configured, Always Configured
Alas, like everything else in life, configurations too change. Endpoints are prone to falling out of line from the established standards or policy. Which is why configuration drift — brought on by updates, user changes, group modifications, etc. — is more the rule than the exception.
 Continuous monitoring and management are necessary to maintain security integrity in our world where 81% of cloud-related breaches exploit misconfigurations.
Continuous monitoring and management are necessary to maintain security integrity in our world where 81% of cloud-related breaches exploit misconfigurations.
Best practice: Continuously monitor endpoints for risky configurations and drift to reduce the risk and severity (à la lateral movement) of breach. Remedio automates configuration security assurance, remediating issues in real time and keeping your current states perfectly aligned with your designed and defined policies.
Myth #6: Business Optimization Is Incompatible With Security Priorities
Many organizations still assume that security initiatives create operational friction — delaying releases, adding red tape, and increasing costs. This outdated thinking frames security and business optimization as mutually exclusive, as if improving one must compromise the other.
While these perceptions may have roots in the past, they don’t reflect modern practices. Today, security enables optimization.
Secure-by-default configurations and continuous monitoring reduce manual effort and human error, freeing IT teams to focus on higher-value projects. True optimization means minimizing both waste and risk — including security risk.
Frameworks like CTEM prioritize exposures based on operational impact, aligning remediation efforts with business objectives. Likewise, architectures like Zero Trust and microsegmentation support agility by enforcing adaptive controls without relying on static perimeters.
In the end, secure systems are more resilient, predictable, and cost-effective — making security a driver of business performance, not a barrier.
Best practice: Smart cyber leaders know they can balance security and operational excellence. Remedio empowers organizations to tighten their security posture without compromising productivity.
Myth #7: It's Someone Else's Job
Figuring out who's responsible for security should be straightforward. Too often it feels like you're stuck in nightmarish version of Abbott and Costello's Who's on First? bit. IT points to Compliance. Compliance points Security Operations. Security Operations point to the vendor.
This confusion is especially common within large organizations, where responsibilities are split across highly specialized teams and personnel. Without clear boundaries and ownership, each team assumes someone else is handling it and critical responsibilities can fall through the cracks.

Organization's may similarly struggle with change management when the changes in question touch multiple departments, or worse, a grey zone. And it's not so much about stepping on toes, but about making smart decisions; something that's impossible to do without an understanding of the dependencies baked into the original setup. Just as often as not, this struggle results in inaction, allowing risks to linger and gaps widen.
Effective cybersecurity is a team sport — and since practically everything has security implications, practically everyone will have to shoulder at least some part of the responsibility. Indeed, every employee, from the SDR to the CISO, is on the field. And when staff isn’t trained or engaged, exposure grows exponentially.
Best practices: Don’t assume. Define. Lay out ownership very clearly and with great detail (especially around the borders) so it's clear who has what handled. You should document who owns which configurations, who approves changes, and who monitors outcomes.
Be sure also to assign clear accountability for educating and supporting the organization's employees on best practices, because security truly is everyone's job.
Myth #8: Hiring More People Will Solve the Problem
Hiring more cybersecurity professionals is often seen as a quick fix to growing cyber threats, but it’s not always the best solution. First off, human error is a core issue. Mo' humans, mo' error.
It's absurd to think you can add more people quickly enough to keep up with (let alone get a leg up on) the growing size and complexity your digital domains. As a transitional strategy, it could make sense, but long-term it just won't work.
Overly manual processes will only make the problem of endless tickets, growing alert fatigue, and exponentially increasing threats worse. And the inefficiencies! Think of the inefficiencies Adding to your headcount typically yields decreasing marginal returns, which makes it a poorly suited solution to a problem of scale.
And more staff won’t help scale your cybersecurity efforts effectively if your systems aren’t designed to handle the increase size, complexity, and speed required of your environment.
Best practices: Instead of hiring more people to triage alerts, focus on automation and optimization. Remedio reduces manual effort and frees up your team to focus on strategic risks — not babysitting spreadsheets.
Myth #9: Endpoint Tools and Firewalls Work Right Out-of-the-Box
While it's tempting to think this, the truth is that default settings weren’t made with your environment or risk profile in mind. And in most cases, "out-of-the-box" means dangerous defaults and under-tuned controls, which puts your enterprise at risk.
Take the 2019 Capital One breach, for example. An attacker exploited a misconfigured firewall on Capital One’s AWS cloud setup, which allowed them to access sensitive data stored in the cloud. This mistake wasn’t a system failure but a configuration error that exposed personal information of over 100 million customers.

Indeed, most tools don’t fail because they’re broken. They fail because they’re misconfigured — silently, persistently, and often without any alert. These gaps can be hard to see, especially in large, complex environments where teams assume everything is working because it hasn’t triggered a red flag.
Best practice: Trust nothing. Validate everything. Remedio helps uncover misconfigurations across security tools you thought were “set and forget” before they become open doors for attackers.
Myth #10: Group Policies Ensure Our Network is Secure.
Relying solely on group policy or Group Policy Objects (GPOs) to secure your environment is a risky proposition. While GPOs are a foundational tool, they often fall short — especially in today’s complex, hybrid IT ecosystems.
Security teams must manage a patchwork of enforcement mechanisms — from GPOs and MDMs to manual scripts and third-party tools — each with different scopes, limitations, and blind spots. This fragmented approach leads to inconsistencies in how policies are applied across operating systems, device types, and user contexts. And it's common, virtually guaranteed, for there to be overlaps, gaps, and conflicts in group policy enforcement.
The result? Critical edge cases where policies aren't applied as intended and you're left exposed.
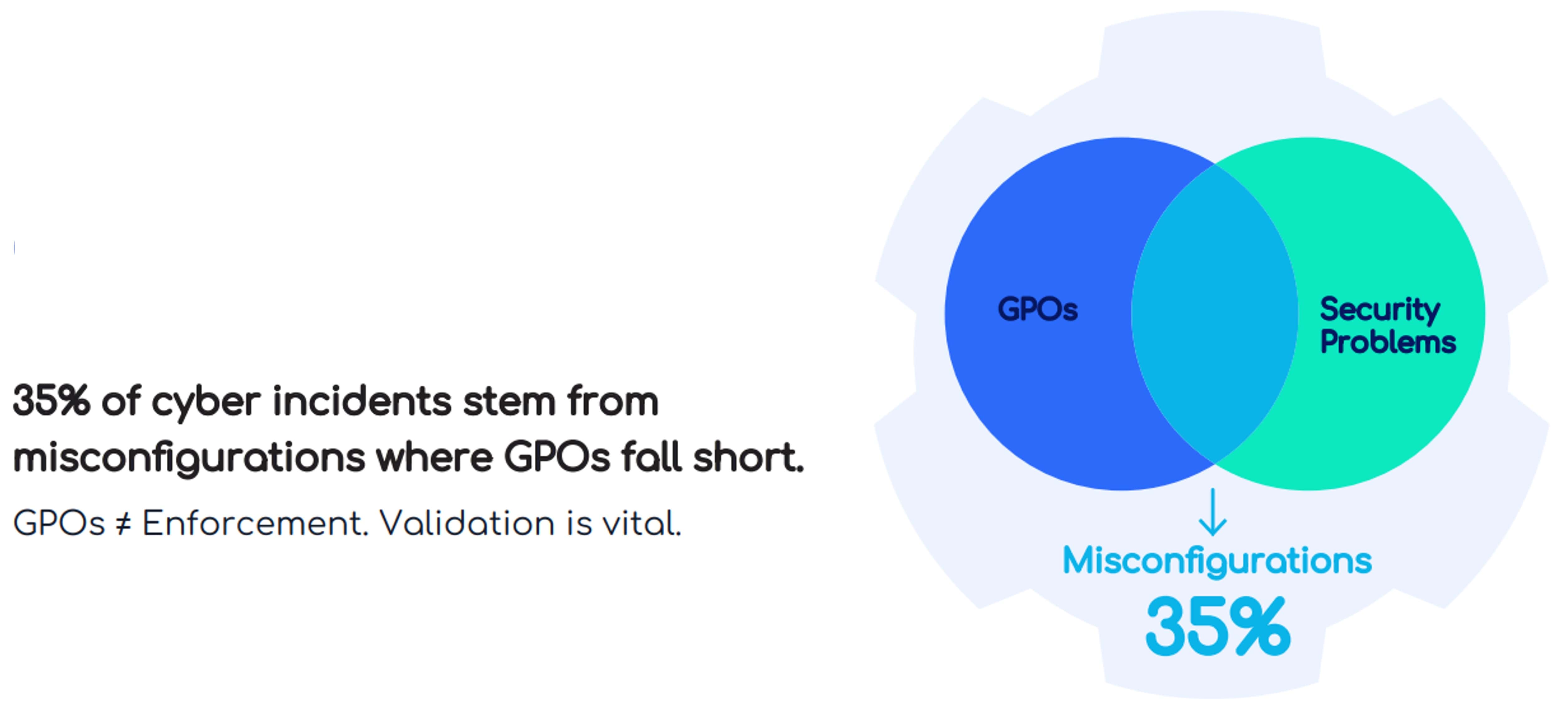
Best practice: Don't assume anything is enforced in the field just because you drew it up that way. You need to actively validate your policies and their enforcement mechanisms for all devices in your fleet.
Bonus Myth: The Cloud Eliminates the Need for Configuration Security.
While the cloud offers flexibility and scalability, it does not automatically eliminate the need for configuration management. Misconfigurations in cloud environments, such as open S3 buckets or improperly set access controls, can still lead to significant vulnerabilities. The reality is, even in the cloud, security is only as strong as its management practices.
In 2020, Estée Lauder suffered a massive data breach due to a misconfigured cloud database. The unsecured database exposed over 440 million records, including sensitive user information, without proper password protection. This breach highlights the ongoing risks of misconfigurations in the cloud, underscoring the importance of managing and securing cloud configurations just as rigorously as on-premise systems.
Best practice: To ensure a secure cloud infrastructure, organizations should implement continuous configuration monitoring and validation. Leveraging frameworks like CIS Benchmarks can guide organizations toward secure and compliant cloud configurations. Always verify settings such as access controls, encryption, and user privileges.
Leaving Cybersecurity Myths Behind
Misconceptions are more than innocent mistakes. In today's threatscape, they’re liabilities. From assuming your tools are working to thinking audits are enough, cybersecurity myths keep organizations badly exposed, playing catch-up, and ultimately less resilient.
Remedio was built to set the story straight and put an end to dangerous cybersecurity myths. With automated misconfiguration detection, proactive drift management, and streamlined protection for complex environments, Remedio helps you break up with false confidence — and finally get secure for real.
About Author

Linda Ivri
Fueled by curiosity, Linda is a senior marketer who thrives on decoding the complex challenges where cybersecurity meets business operations.
Subscribe to
our Newsletter
We are ready to help you until and unless you find the right ladder to success.
Related Posts
Join over 25,000 in beating the failure of strategies by following our blog.
If a threat falls in the SOC and no one ties it to revenue, does it really make ...
7 minute read
Picture the legendary Metropolitan Opera House on opening night. The air hums wi...
6 minute read
In cybersecurity, the smallest missteps can lead to the biggest breaches. Take B...


.jpg?width=5211&height=2406&name=it-operations-productivity-improvement-min%20(4).jpg)









Comments