Security leaders invest heavily in the front door: phishing defenses, malware de...
Simple Steps To Stop Privilege Escalation from Moving Laterally

In my previous article I wrote about the importance of monitoring all endpoints in the organization for the existence of cached credentials. In this post, I'm going to explain what you can do to quickly close your exposure when such caching is found.
If you are locally storing credentials, hackers can easily reveal the hash using Mimikatz. Then, the attacker can use the “pass the hash” technique to gain access to remote machines and services.
Grinding the Attack to a Stop
Here' how the attack path breaks down and what you can do to stop it:
- Mimikatz and similar tools are only able to access the credential hashes when run as a privileged user such as a local administrator.
Mitigation action: minimize privileged user access where possible.
- Microsoft desktops and servers have a configuration known as the Debug Privilege. This is a security policy setting that allows users to attach a debugger to a process or to the kernel.
For example, with debug privilege, one can silently remove all the security agents installed on a device, without raising any alert.On many versions of Windows, including Windows 10, Debug Privilege is assigned to the Built-in Administrators group by default!
That is a great power in the hands of whoever wants to spread their ransomware in your organization.
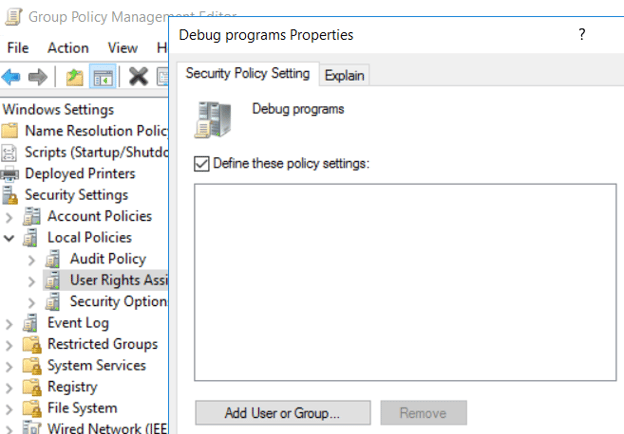
Mitigation action: Apply GPO and revoke the debug privilege from all users:
Group Policy Management Editor → Windows Settings → Security Settings → Local Policies → User Rights Assignment → Debug programs → Define these policy settings → Leave the box empty and press OK
Think Like a Hacker to Beat the Hacker
When an attacker gains a privilege escalation on one of your endpoints, it’s already bad news. They will then try to leverage that power for making a lateral movement inside your network and take over additional workstations and servers.
Still, by applying the right practices on your endpoints, the attacker’s chances are slim.
Remedio always monitors and reports on all endpoints in your organization. We can tell if the debug privilege is not secured properly including whether the policy has also been successfully applied.
About Author

Inbal Pearlson
Subscribe to
our Newsletter
We are ready to help you until and unless you find the right ladder to success.
Related Posts
Join over 25,000 in beating the failure of strategies by following our blog.
If a threat falls in the SOC and no one ties it to revenue, does it really make ...
7 minute read
Picture the legendary Metropolitan Opera House on opening night. The air hums wi...
6 minute read
In cybersecurity, the smallest missteps can lead to the biggest breaches. Take B...







Comments