At a time when cyber threats are increasingly sophisticated, understanding and i...
Introduction
The cyber threat landscape has been significantly heightened by the emergence of LockBit 2.0, an advanced and pernicious form of ransomware.
Since its inception as a Ransomware-as-a-Service (RaaS) in 2019, evolving into LockBit 2.0 in June 2021, this ransomware has led to approximately 1,700 attacks against U.S. organizations, extorting roughly $91 million since 2020.
LockBit 2.0, recognized as the leading global ransomware threat in 2022, has targeted a broad array of critical infrastructure sectors, including government, education, healthcare, and more, highlighting the need for effective cybersecurity measures.
This blog, informed by insights from CISA and recent reports, explores LockBit 2.0’s complexities and how GYTPOL’s innovative solutions provide robust defenses against this evolving cyber menace.
Here, we will focus on a really insightful report that was published by CISA, Understanding Ransomware Threat Actors: LockBit
Delving into the latest LockBit2.0 incidents, the article offers valuable insights on:
🔍 Technical details
📊 Statistics
🛡️ Mitre Attack Techniques
Crucially, it emphasizes Mitigation strategies!
The Emergence of LockBit 2.0
LockBit 2.0 represents an evolution in ransomware sophistication.
Building upon the disruptive capabilities of its predecessor, it has been increasingly targeting a wide range of sectors globally.
LockBit 2.0, as a Ransomware-as-a-Service (RaaS), allows affiliates to launch attacks using enhanced tools and infrastructure, making its detection and mitigation more challenging.
Technical Intricacies of LockBit 2.0
The technical prowess of LockBit 2.0 lies in its ability to exploit misconfiguration vulnerabilities in commonly used applications and systems.
By abusing known CVEs like Apache Log4j and leveraging exploits in RDP, LockBit 2.0 gains unauthorized access and control over systems. This capability is further augmented by its use of sophisticated techniques for lateral movement, such as Cobalt Strike, and its ability to manipulate and clear Windows Event Log files to cover its tracks.
GYTPOL’s Proactive Defense Against LockBit 2.0
In response to the multifaceted nature of LockBit 2.0, GYTPOL has developed a comprehensive strategy as per the CISA report GYTPOL provides curation and mitigation mapped to the MITRE ATT&CK framework
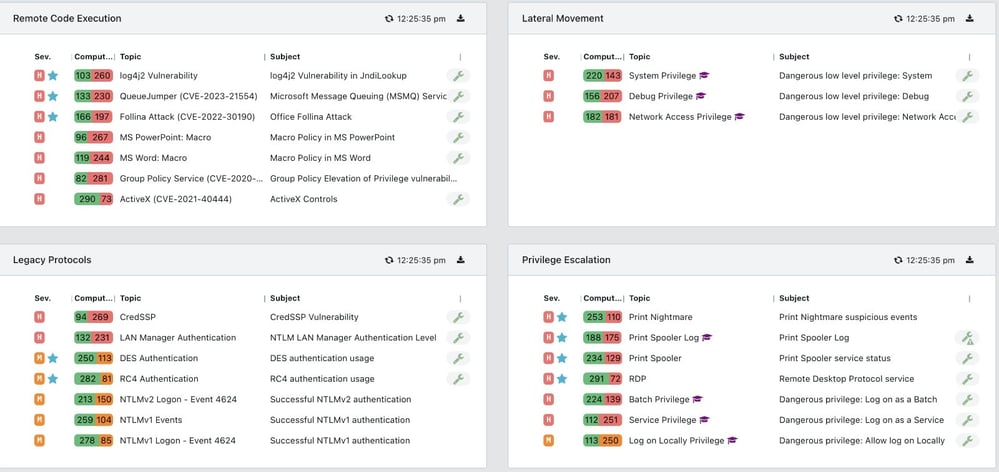
- Active Directory Protection: By continuously monitoring and rectifying device misconfigurations in the Active Directory, GYTPOL prevents one of LockBit 2.0’s primary attack vectors.
- Dynamic Threat Detection and Remediation: GYTPOL’s systems are designed to detect and remediate the exploitation of misconfiguration vulnerabilities and abuses of system features, a common tactic of LockBit 2.0.
- Advanced Alerting and Monitoring: Our solutions are equipped to identify and alert on suspicious activities that are indicative of LockBit 2.0 attacks, such as unusual changes in the Windows Event Log files.
- Stringent Access Controls and Policy Enforcement: GYTPOL enforces robust access control and auditing measures, significantly reducing the risk of unauthorized access and lateral movement within the network – a tactic frequently used by LockBit 2.0.
- Regular Compliance and Security Assessments: Keeping pace with evolving threats, GYTPOL ensures that organizations’ security measures align with the latest standards, providing an added layer of defense against sophisticated ransomware like LockBit 2.0.
LockBit 2.0, with its enhanced capabilities, poses a serious threat to organizations worldwide. However, with GYTPOL’s comprehensive and proactive cybersecurity solutions, businesses can effectively shield themselves against this sophisticated ransomware. By staying ahead in detection, remediation, and compliance, organizations can ensure their resilience against such advanced cyber threats.
About Author
Simone Lavi
Want updates?
Subscribe to our monthly newsletter to stay up-to-date and in the loop on all things configurations security.
Related Posts
Join over 25,000 in beating the failure of strategies by following our blog.
In the fast-paced world of technology, where innovation is a constant, it’s cruc...
4 minute read
Introduction:
6 minute read
In the complex world of mergers and acquisitions (M&A), where cybersecurity ...


Comments